You can’t get em all. The onslaught of bad actors on our IP’s and servers is astounding. I watch a lot of the old goo.gl Honeypots (Project HoneyPot/Cloudflare) I set up years ago still sending bots and nets to hell. It’s a valiant effort I think, since I’m only one against millions and the others who help in the fight against the bad guys all together is making a difference.
So what do we have here? 2 ASN blocks which is a great way to stop a pretty big slice of “Chinese?” hackers…. in the end it could be an American or Turk for all we know tunneling through but it’s a Chinese network in this short blog post.
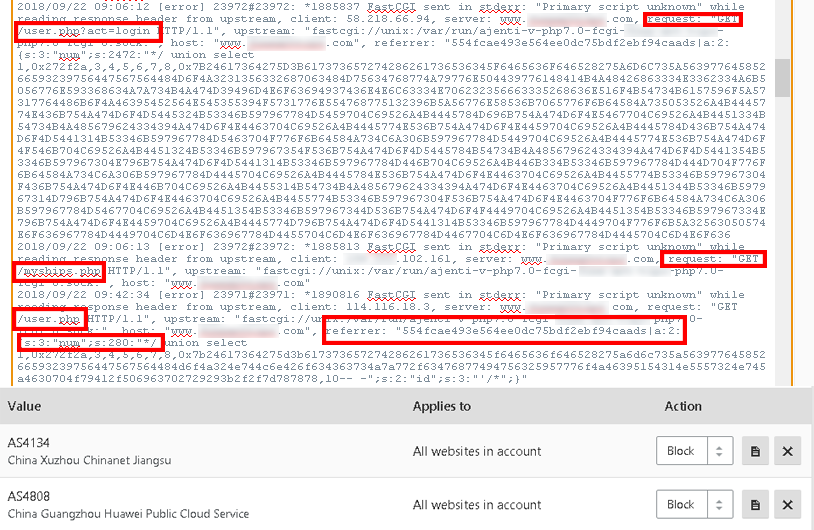
Take a look.
We’ve got
AS4134
China Xuzhou Chinanet Jiangsu
&
AS4808
China Guangzhou Huawei Public Cloud Service
from the IP’s in those ranges from our PHP7 NGINX Error log – 58.218.66.94
NICE – On Project honeypot We don’t have data on this IP currently. If you know something, you may leave a comment. (that’s a project link, not this post).
How did we get that? From the error log earlier today. You can see them pushing some sort of login request to a non-existent php script which obviously is being injected into other not so secure sites creating the intended botnet. I take this seriously so as I said earlier this is one persons way of at least challenging the bad out there and securing an important client site which we know she appreciates from past bad experience on Bluehost. They don’t/won’t help without money.
Am I bad mouthing the competition, you betcha the file system and database was so cluttered with absolute nonsense anybody that knows what a clean WordPress install would shudder to see that mess. It’s all by the way (as are other big hosting outfits) by design, to confuse the precious consumer so much that all they can do is pay and hope to find someone willing to help (which their support staff is trained to not speak candidly because frankly they have not a clue about WordPress or hacking). That’s exactly how we get our business at Wordsrack, people come to us after a really bad experience or worse, they got hacked and found us through our great friends and customers now coast to coast across the US and Canada.
We grew because our system is elegant AND un-cluttered. And we pay attention to our system and error logs, pro-active against hackers and use the best tools in the world to keep you safe. We are a certified Cloudflare hosting partner which means on top of us thwarting attacks on a hardened setup we have a great worldwide anti-DDOS wall around the fort and our clients are sped up using free railguns* and https.
Here’s the actual snapshot of the NGINX PHP7 Log
The beauty of the bottom of that image is the jail we can create around thousands of potentially bad IP’s. I don’t mind for a minute stopping a whole organization from hitting a client site and like to learn from the vectors as we try to push the needle more in our favor each day. See more about the ASN’s below.
AS4808 ??
The dirty TruthRevealed
inetnum: 114.116.0.0 – 114.116.255.255
netname: HWCSNET
country: CN
descr: Huawei Public Cloud Service (Huawei Software Technologies Ltd.Co)
Oh, did you read lately that the US government doesn’t want you to support Chinese Phone manufacturers? Wonder why? Huawei is frankly in this business and don’t look like the good guys.